ICTO’s security team has brought vulnerability assessments, audits and penetration test into periodical task plan since 2016, to protect and secure the information technology assets of university. Penetration test (also called pen testing) provides a realistic assessment of existing computer system, network or application to identify vulnerabilities and exploits that may be present. Its main objective is to determine security weaknesses.
Based on the tests performed by ICTO, vulnerabilities and weaknesses in the system are usually identified before they are exploited by the hacker. ICTO tries every effort to take effective countermeasures to fix the vulnerabilities and weaknesses. Besides the Penetration Test, to avoid attacks through known issues or vulnerabilities, ICTO regularly reviews updates from vendors and makes sure that the latest security patch/hot-fix are applied to the operating system and applications timely. We also take proactive security monitoring to reduce risk of new vulnerabilities and zero-day attacks.
How is Penetration Test Performed?
In December, 2016, ICTO had conducted first phase of Penetration Test. The preliminary results show no flaws were revealed from our systems.
The second phase of Penetration Test is still in progress and the result will be concluded in this month. The schedule will exclude some special periods, such as examination, enrollment and special events, etc.
Scope
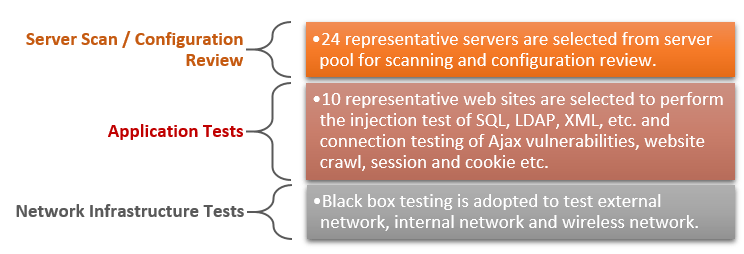
Approaches
The test methods of Penetration Tests are driven by techniques and similar approaches used by hackers to penetrate our computer systems. Penetration tests verify the presence of flaws and confirm the security measures.
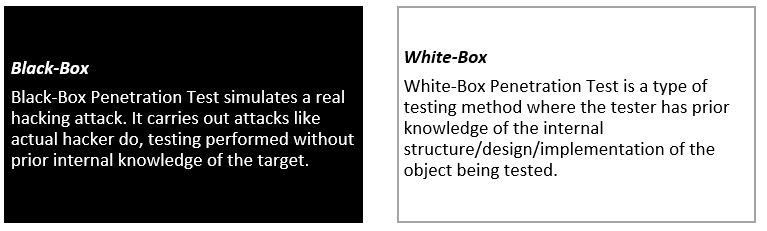
Penetration testing can be conducted in several ways, commonly accepted approaches are Black-box & White-box testing.
The results of a penetration test can help us strengthen our computer network infrastructure in areas of security.