Phishing definition on Wikipedia refers to the attempt to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money), often for malicious reasons, by masquerading as a trustworthy entity in an electronic communication.
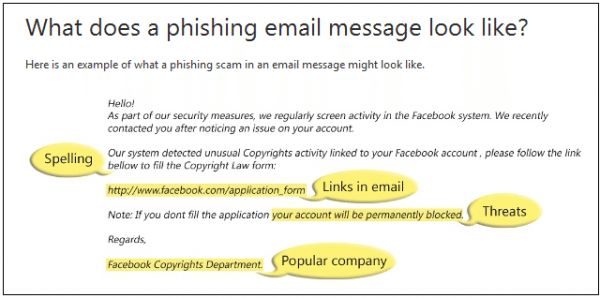
Source: http://www.microsoft.com/security/online-privacy/phishing-symptoms.aspx
Some phishing emails are easy to identify due to spelling mistakes and bad grammar contents. In the past, it used to be one of the criteria to identify phishing email. However, as phishing contents are becoming more accurate and precise, it is not so easy relying on this clue alone.
Links in the phishing email provide another clue. If there is a link in a suspicious email message, please do not click on it. Links may lead you to an executable (.exe) file. These executable (.exe) file are believed to spread malicious software.
Threats are another clue as you may find that phishing email require you to do something followed with a threat that if you do not follow the link or do not provide certain information, your computer account or bank account will be closed.
Spoofing popular websites or companies names are another clue as email appears to be from a legitimate corporation, business or a popular website but actually take you to phony scam sites or legitimate-looking pop-up windows.
Recently, there were several phishing emails disguising under the name of ICTO Help Desk. There are also phishing emails disguised as if it is from an academic institution, courier service and banks. We are thankful to staff who have been regularly reporting phishing emails to us for checking. We would like to remind you not to disclose your personal information, banking details, your password and other sensitive information to any illegitimate requester or anyone you are not sure about the identity. Most of all, ICTO will never send an email requesting your password.
Here are some of the most popular types of phishing emails:
- Conference registration. Request to provide account details.
- Call for papers. Email is sent using Yahoo or Gmail.
- Webmail storage is low and/or your email quota is reaching its limit. Request user to input or confirm account information to increase quota.
- A virus is detected. Request to follow a link to scan your computer’s hard disk.
- Transfer to new email account. Request to provide account information.
- Winner of a lottery. Winner of Google lucky draw. Request to provide personal details and account information to claim your reward.