E-mail is one of the popular Internet application. Un-solicited massive e-mails (spam), e-mail viruses and phishing emails created the following problems that affect our users and computer systems:
- Reducing mail user’s productivity
- Endangering mail user’s computer
- Consuming storage of mail server
- Consuming bandwidth of network
Although it is impossible to completely stop spam, there are ways to combat spam and e-mail viruses. ICTO deployed the Secure Email Gateway (first introduced in 2006 and further enhanced in 2016) to inspect all incoming and outgoing emails of the University email systems. It is an anti-spam and anti-virus solution implemented at network level. At user level, ICTO also enabled anti-spam function of ESET Endpoint Security for office computers. Both solutions setup a Two-Level Protection of Malicious Email.
Mechanism of Secure Email Gateway:
1. How does the Secure Email Gateway detect unwanted emails? How is privacy concerned?
Secure Email Gateway uses powerful anti-spam and anti-virus engine with variety of sophisticated techniques including pattern matching, heuristics and emulation to detect spam, viruses, malware, phishing scams and other unwanted emails. Privacy is guaranteed in the process of scanning spam and virus by the Secure Email Gateway. No user email content is inspected by any person.
2. What are the functions of Secure Email Gateway?
The Secure Email Gateway is an anti-spam and anti-virus solution implemented at network level. All emails send from internet (external) and deliver to your “@umac.mo”, “@docs.umac.mo”, “@wkg1.umac.mo” and “@umac.edu.mo” e-mail addresses are inspected by Secure Email Gateway.
Functions of Secure Email Gateway:
- Detect and quarantine the suspected emails.
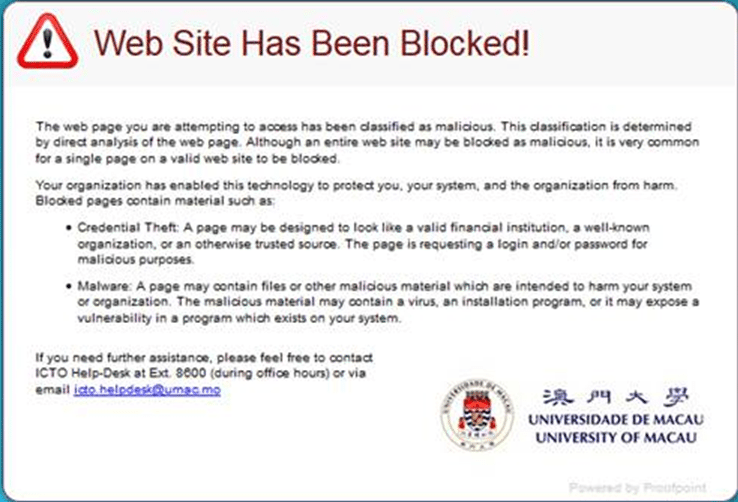
- Protect users from phishing and targeted attacks with URL Defence. If the links in the email are malicious, the notification will be prompted up in the browser to notify users that the website has been blocked.
- Store suspected emails in personal quarantine folder for 30 days to let users inspect the quarantined emails in a safe environment and decide whether to release the emails.
- Send daily digest of suspected emails stored in the last 24 hours.
- Allow users to setup their own policy to whitelist/blacklist specific sender.
- Allow users to select their own preference whether to quarantine bulk messages such as promotions newsletters and other bulk emails.
3. What Email Security Precautions have been implemented with Secure Email Gateway?
Zero day threat protection
When new malware appears, the signatures for identifying it is usually not available right away. Hacker usually will make use of this gap to perform targeted attacks. It is necessary that our Secure Email Gateway will hold the suspected virus emails for a short period of time and wait for virus inspection. Most of the virus signature can be ready in 12 hours after malware emerges.
Malicious Email Quarantine
The malicious and unsolicited emails are quarantined at Secure Email Gateway for a period of time. Those expired emails will be purged from the system and cannot be retrieved again. Therefore, we recommend user to review quarantined emails periodically.
Targeted Attack Protection
Some of the sophisticated phishing emails cannot be detected by content inspection since the content of the email is clear (not like the spam), even so, the links (URL) in each email is checked using a variety of sophisticated techniques. The URL is rewritten and it causes the Secure Email Gateway’s URL Defence to check the linked website when user clicks on the URL. If the website is malicious, a message is prompted in user browser to notify user that the website is blocked.
Prevention of sending/receiving email with auto-executable attachments (e.g. exe, .vbs, etc.) (Click here for details)
The auto-executable attachments are commonly used to transmit viruses and malware. To prevent the recipient from downloading and running the malicious program, the auto-executable attachments are not allowed to send/ receive via email.
To send out these types of attachment, the sender can rename the file extension with a file extension that our system does not treat as a threat. (E.g. renamed the file extension from .exe to .tmp). Once the file is received, the recipient can save the file as .exe and open the executable file manually.
Prevention of email spoofing
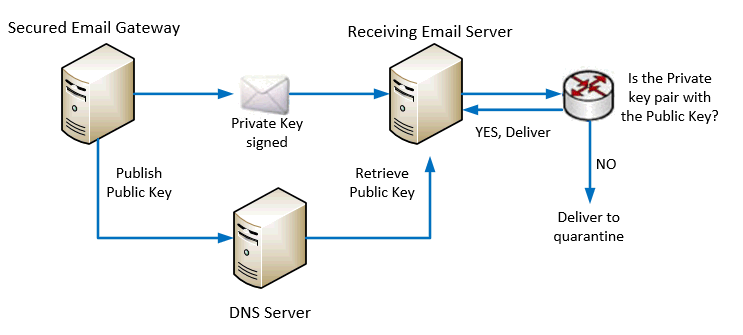
It is intended to prevent forged sender addresses in emails, which is often used by phishing and spam emails. It works by checking whether an email claimed to come from a specific domain was authorized by the owner of that domain or not.
One of the method used is by DKIM cryptographic authentication technology as illustrated below.
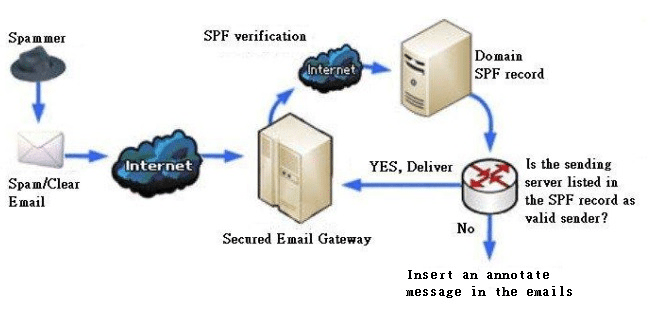
Another method used is SPF which is a simple email-validation system to allow mail receiving servers to check whether an incoming mail from a host is authorized by the domain’s administrator or not.
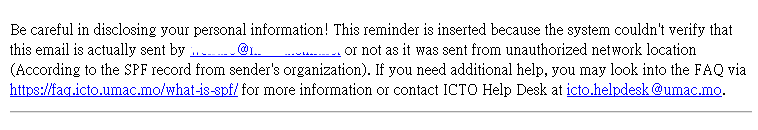
If the email fails SPF authentication, a reminder is inserted in the email. Therefore, if user sees a message as below, be careful in disclosing personal information! Other organizations who enable the SPF checking will also insert reminder to, quarantine, or even reject such emails for protecting their users.
 Bounce back verification
Bounce back verification
Our Secure Email Gateway check every bounce email to ensure that the original email was sent by us. Bounce back email that was not originated from our email servers will be rejected.
Prevention of outgoing malicious email
From time to time, it is detected that hackers send spam emails with the compromised UM accounts. Email security vendors will monitor the Internet traffic and identify spam email sending servers. If they detect spam emails sent from our email servers, they will lower our reputation (a scoring method). If our reputation is low, most of the email service providers will reject the emails sent from our users. To prevent it from happening, our Secure Email Gateway will check every outgoing email and drop all malicious and unsolicited emails
Why can’t I access the links in User Digest via Internet?
For security reasons, the links in User Digest are only accessible on campus network.
If you need to access the links off campus, please connect your computer to the UM campus network by using SSL-VPN client. For details, please visit https://icto.umac.mo/network/ssl-vpn/.
Once your computer is connected to UM Network, you can release or manage the quarantined emails via your “User Digest” or Web Portal at https://umemppm.umac.mo/.
The University’s Email Security Status
The computer network attacks have become more frequent and severe in recent years. The University keeps receiving phishing emails targeting at our users. In 2017, only 12.75% of the incoming emails were clean (not categorized as spam, virus emails or other unwanted emails). 87.25% of incoming emails were detected as malicious email and stopped by our secure email gateways.
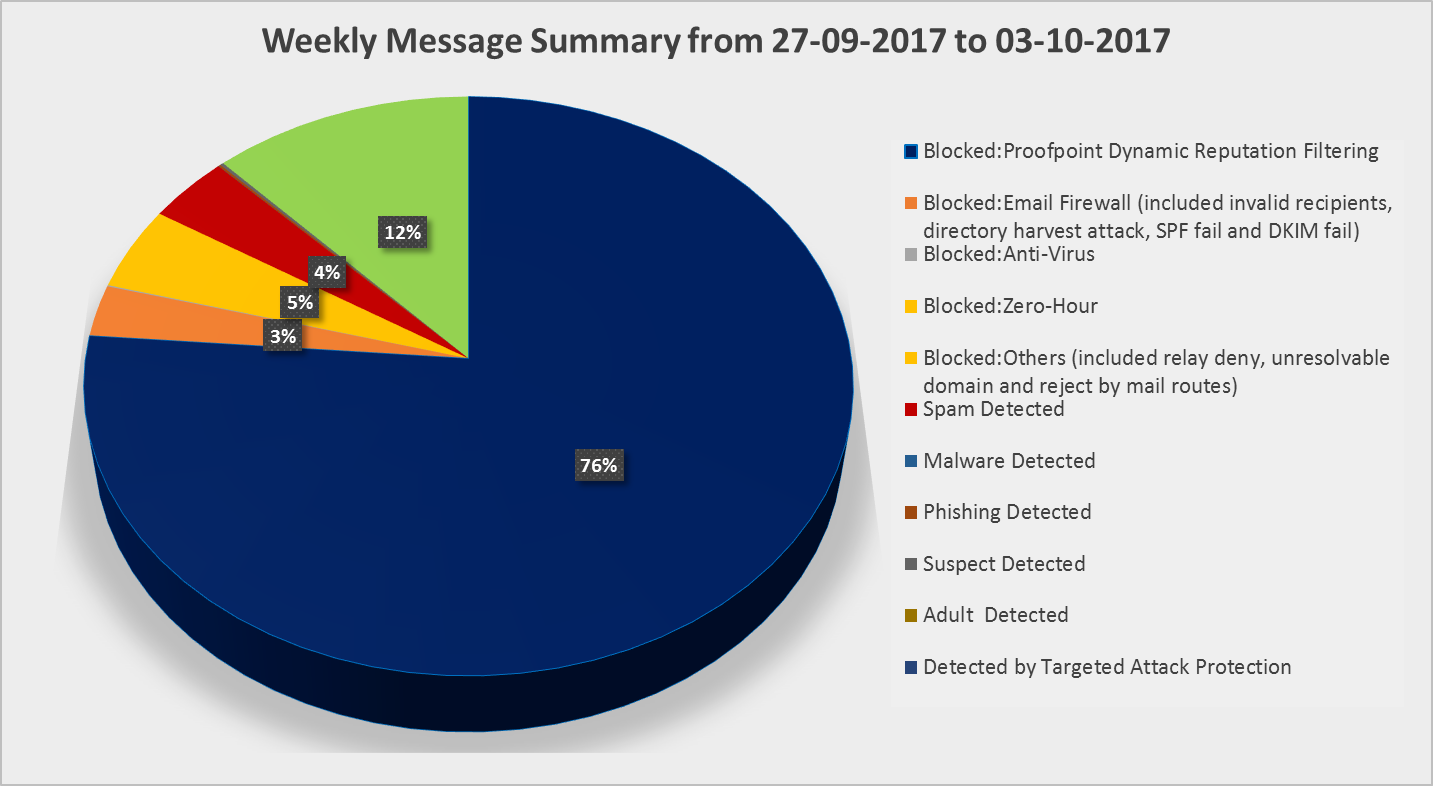
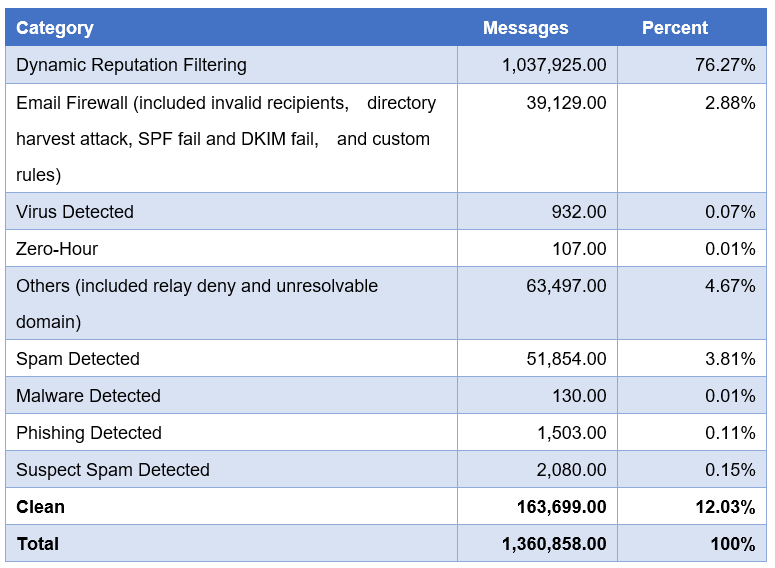
The above chart and table show the message summary in a week. As you can see, most of the messages were stopped by the dynamic reputation filtering. Dynamic reputation filtering is a powerful email sender reputation management service that combines a global email sender IP reputation, the email sender IP reputation data is analysed by powerful machine learning algorithms to block connections from malicious IP addresses. It is also the first line of defence against spam emails, denial-of-service, other email-borne and attacks.
The other messages were blocked due to the invalid recipients, directory harvest attack, relay deny, unresolvable domain and mail routes.
Recent changes on Secure Email Gateway
In response to user feedback, we fine-tune the phishing definition by creating additional system rules and revised the SPF policy by adding alert to suspected email instead of quarantining the email. We will keep collecting user feedback and do our best to balance email safety and user convenience.
Want More Information?
- Web Page about Email Security
- User Guide of Malicious Email Quarantine Function
- Frequently Asked Questions about User Digest and Web Portal of Secure Email Gateway
- Frequently Asked Questions about ESET End-point security for office computers


