The Internet technology is evolving rapidly and getting sophisticated with the technological advancement in recent years. Users, system administrators and managers are faced with the ever-changing hacking techniques on regular basis. In this rapidly changing IT environment, the traditional methods may not be sufficient to defend against the increasing and more severe cyberattack scenarios.
In 2018, phishing scams and network attacks have rapidly grown posing huge threat to global information security (IS). ICTO has reviewed existing information security related safeguards, internal controls and deficiencies. ICTO carried out the rearrangement of existing equipment and internal control procedures as well as made-up to tackle the deficiencies. We have also taken some measures to protect against the phishing attacks and other IS threats.
| Details | |
| 11 Meetings & Briefings | Held meetings and briefings with committees and task teams to keep raising IS awareness |
| 9 Tasks |
|
| 8 Guidelines /Procedures | Released totally 8 guidelines or procedures to cover system security, user account security, IS incident handling, data protection, asset management, IT crisis management and contingency, and self-assessment |
| 7 Studies |
|
| 4 IS Awareness Monthly Tips | |
| 2 Sessions | Information Security Seminar 2018 (Seminar Content | Training Events) |
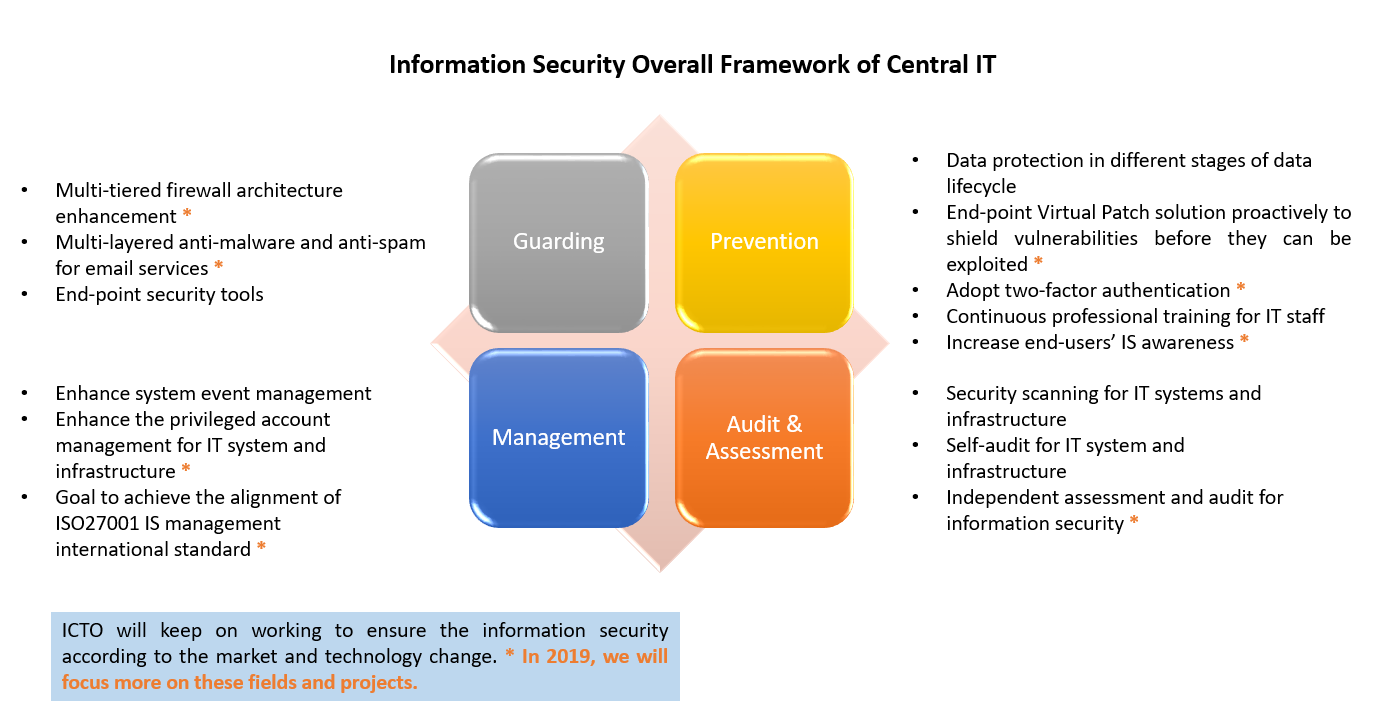
| 1 Framework | Four major principles: “Guarding”, “Prevention”, “Management” and “Audit & Assessment” |
Plan for Coming Years
ICTO will keep performing regular IS related tasks to ensure information security. Moreover, we will keep an eye on the trend of market change, technology change and timely adjust the IS strategy.