Computer network attacks are becoming common incidents and more severe in recent years. We continuously receive a large number of phishing emails targeted to deceive unsuspecting users. Every day, there were over 85% of incoming emails classified as malicious or unsolicited emails.
To enhance the email security, ICTO has deployed a Secure Email Gateway to inspect all incoming and outgoing emails of the University email system since last year and implemented Multi-Layered Quarantine of Malicious Email in October this year. It is intended to provide our users with more security and flexibility in handling the suspected emails.
How does Two-Level Protection Protect You from Malicious Email?
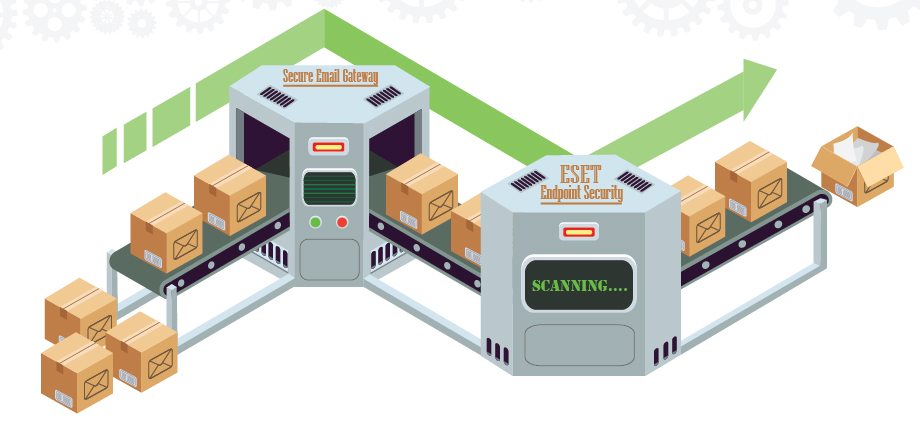
The Secure Email Gateway serves as the First-Level Protection at the inbound (receiving) of our campus email infrastructure. If the system detects any incoming malicious or unsolicited email, the email is quarantined at the Secure Email Gateway. The quarantined email will appear in your personal quarantine folder and display in “User Digest” email. You can release or manage the emails via Secure Email Gateway Web Portal at https://umemppm.umac.mo/ or “User Digest” email. The Secure Email Gateway will scan the message with the latest signatures before releasing to your mailbox.
When an email arrives at your mailbox, ESET Endpoint Security Client inspects it as Second-Level Protection. If ESET finds any suspected email in your inbox, the email is immediately moved to [Junk Email] folder.
Where shall you find the quarantined email?
|
Zero Day Threat Protection
When new malware appears at the zero day, the signatures for identifying it is usually not available yet. Hacker usually will make use of this gap to perform targeted attacks. It is necessary that our Secure Email Gateway will hold the suspected virus emails for a short period of time and wait for virus inspection. Most of the virus signature can be ready in 12 hours after malware emerges.
Targeted Attack Protection
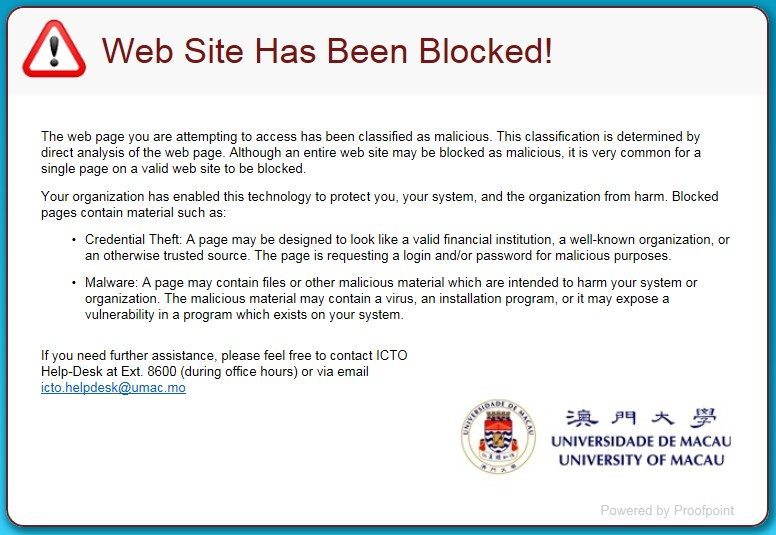
Some of the sophisticated phishing emails cannot be detected by content inspection since the content of the email is clear (not like the spam), even so, the links (URL) in each email is checked using a variety of sophisticated techniques. The URL is rewritten and it causes the Secure Email Gateway’s URL Defense to check the linked website when user clicks on the URL. If the website is malicious, a message is prompted up in user browser to notify user that the website is blocked.
Highlights of Malicious Email Quarantine at Secure Email Gateway:
- The malicious and unsolicited emails are quarantined at Secure Email Gateway
- You can safely preview the malicious emails in your personal quarantine as the preview is performed at Secure Email Gateway
- You can set up your own safe or blocked senders lists at Secure Email Gateway
- You can have quick information about the quarantined emails from “User Digest” send to you daily
- You can manage the quarantined emails either by directly accessing the links at “User Digest” or by logging in to the Secure Email Gateway Web Portal https://umemppm.umac.mo/
- You can select your own spam policy via Secure Email Gateway Web Portal according to your preference
- The malicious emails are held in quarantine of Secure Email Gateway for a period of time. Those expired emails will be purged from the system and cannot be retrieved again. Therefore, we recommend you to review your quarantined emails periodically
Other Email Security Precautions
In addition to the Malicious Email Quarantine, ICTO also implemented the following email security precautions simultaneously:
1. All product promotions, e-Newsletters and other bulk emails will be quarantined automatically by default.
Based on the survey result, most users classified the commercial promotions, e-Newsletter and large quantities of emails as spam/ unwanted email. All kinds of bulk emails are quarantined automatically by default.
If you want to receive some of the bulk emails, you can select the email and click “Release and Safelist” via Web Portal at https://umemppm.umac.mo/ or “User Digest” email.
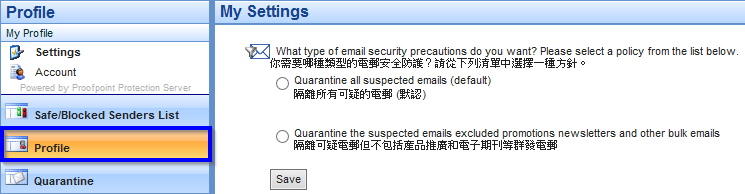
In addition, there is an option to let you exclude all bulk emails from spam detection at the Secure Email Gateway Web Portal if you would like to receive bulk emails in your mailbox.
Please login to the Web Portal, click the “Profile” tap on lower left corner and select your spam policy in “My Settings” page.
2. Prohibition of sending/ receiving email with auto-executable attachments (e.g. exe, .vbs, etc.) (Click here for details)
The auto-executable attachments are commonly used to transmit viruses and malware. To prevent the recipient from downloading and running the malicious program, the auto-executable attachments are prohibited to send/ receive via email.
To send out these types of attachment, the sender can rename the file extension to use a file name extension that our system does not treat as a threat. (E.g. renamed the file extension from .exe to .tmp). Once the file is received, the recipient can save the file as .exe and open the executable file manually.
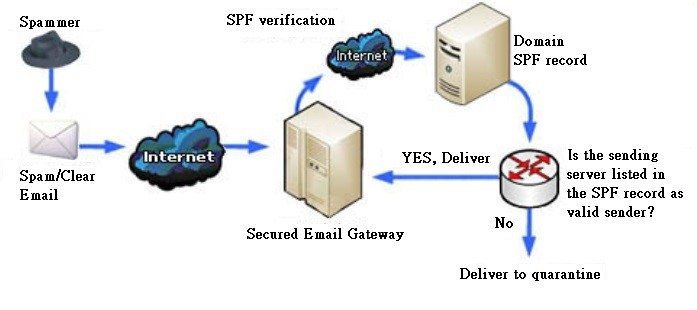
3. Prevention of email spoofing by enabling DKIM (Domain Keys Identified Mail) and SPF (Sender Policy Framework) checking
It is intended to prevent forged sender addresses in emails, which is often used by phishing and spam emails. It works by checking whether an email claimed to come from a specific domain was authorized by the owner of that domain or not.
One of the method used is by DKIM cryptographic authentication technology.
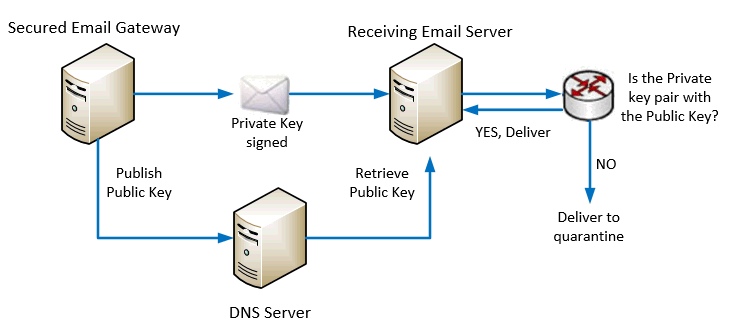
Another method used is SPF which is a simple email-validation system to allow mail receiving servers to check whether an incoming mail from a host is authorized by the domain’s administrator or not.
4. Prevention of email spoofing by enabling bounce back verification
Our Secure Email Gateway check every bounce back email to ensure that the original email was sent by us. Bounce back email that was not originated from our email servers will be rejected.
5. Prevention of outgoing malicious email
From time to time, hackers send spam emails with the compromised UM accounts. Email security vendors will check the Internet traffic and identify spam email sending servers. When they detect spam emails sent from our email servers, it will affect our reputation (a scoring method). If our reputation is low, most of the email service providers will block the emails sent from our users. Therefore, our Secure Email Gateway will check every outgoing email and block all malicious and unsolicited emails.
Want More Information?
- Web Page about Email Security
- User Guide of Malicious Email Quarantine Function
- Frequently Asked Questions about User Digest and Web Portal of Secure Email Gateway
- Frequently Asked Questions about ESET End-point security for office computers
- Frequently Asked Questions about the prohibition of sending email with executable attachments