Trend Micro defines Ransomware as “A type of malware that prevents or limits users from accessing their system, either by locking the system’s screen or by locking the users’ files unless a ransom is paid. More modern ransomware families, collectively categorized as crypto-ransomware, encrypt certain file types on infected systems and forces users to pay the ransom through certain online payment methods to get a decrypt key”.
Ransom Prices and Payment
Due to the anonymity offered by cryptocurrencies Ransomware operators commonly required ransom payments in bitcoins. However, recent ransomware variants list alternative payment options such as iTunes and Amazon gift cards. Please note that ransom payment does not guarantee that users will get the decryption key or unlock tool required to regain access to the infected system or hostage files.
Ransomware Infections
According to the report published by TrendMicro’s report 1H 2016, in the first half of 2016 there was an increase of 172% in ransomware families compare to previous year.
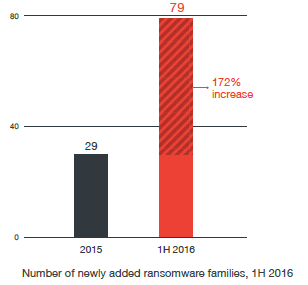
Source: Trend Micro – Reign of Ransomware – 2016 1H Security Roundup
Due to interconnectivity of the devices and access to Internet and intranet, there are several ways your computer can get infected with ransomware. It could be when you visit a malicious or compromised website. Ransomware may arrive with other malware when you download a program or a document from Internet. Due to popularity of emails in business and personal communication, ransomware is often delivered as an attachment via spammed email or it is downloaded from malicious pages through malvertisements.
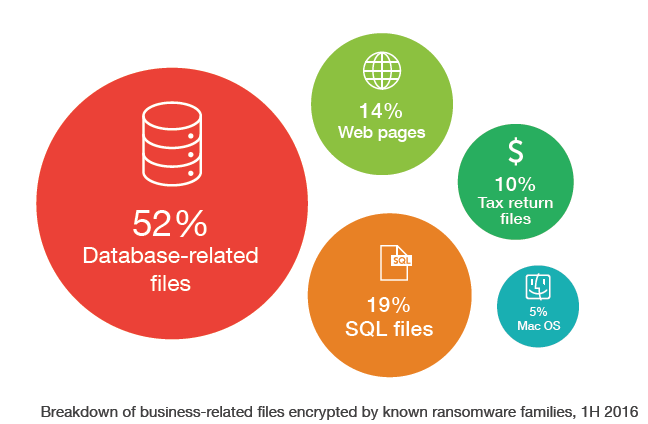
Source: Trend Micro – Reign of Ransomware – 2016 1H Security Roundup
What Happens if your Computer is Infected
Once file containing ransonware is executed in the system, ransomware can either lock your computer screen, or in the case of crypto-ransomware, encrypts specific types of files. When a computer is infected with crypto-ransomware, a full-screen notification is displayed on the infected system’s screen. An image covering the screen prevents victims’ from using their computer. Screen also displays the instructions, how one can pay the ransom. Other type of ransomware prevents access to files saved in the hard disk of the computer.
Evolution of Ransomware
As we described earlier that the Ransonware is any malware that prevents or limits users from accessing their system, either by locking the system’s screen or by locking the users’ files unless a ransom is paid. In recent years, malware have evolved with technological advancements. Reveton is a ransomware. It impersonates or disguises as law enforcement agencies. It is also called Police Ransomware or Police Trojans. When computer is infected with malware, it shows a notification page as if it is from the victim’s local law enforcement agency. It conveys to the victims that they were caught doing an illegal or malicious activity on Internet. Reveton variants track the geographical location of their victims.
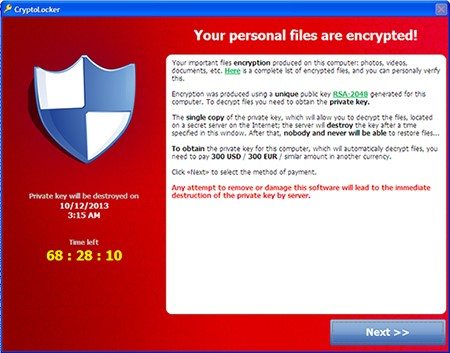
Source: http://www.trendmicro.com/vinfo/us/security/definition/Ransomware
Ransomware Infections

Source: http://www.trendmicro.com/vinfo/us/security/definition/Ransomware
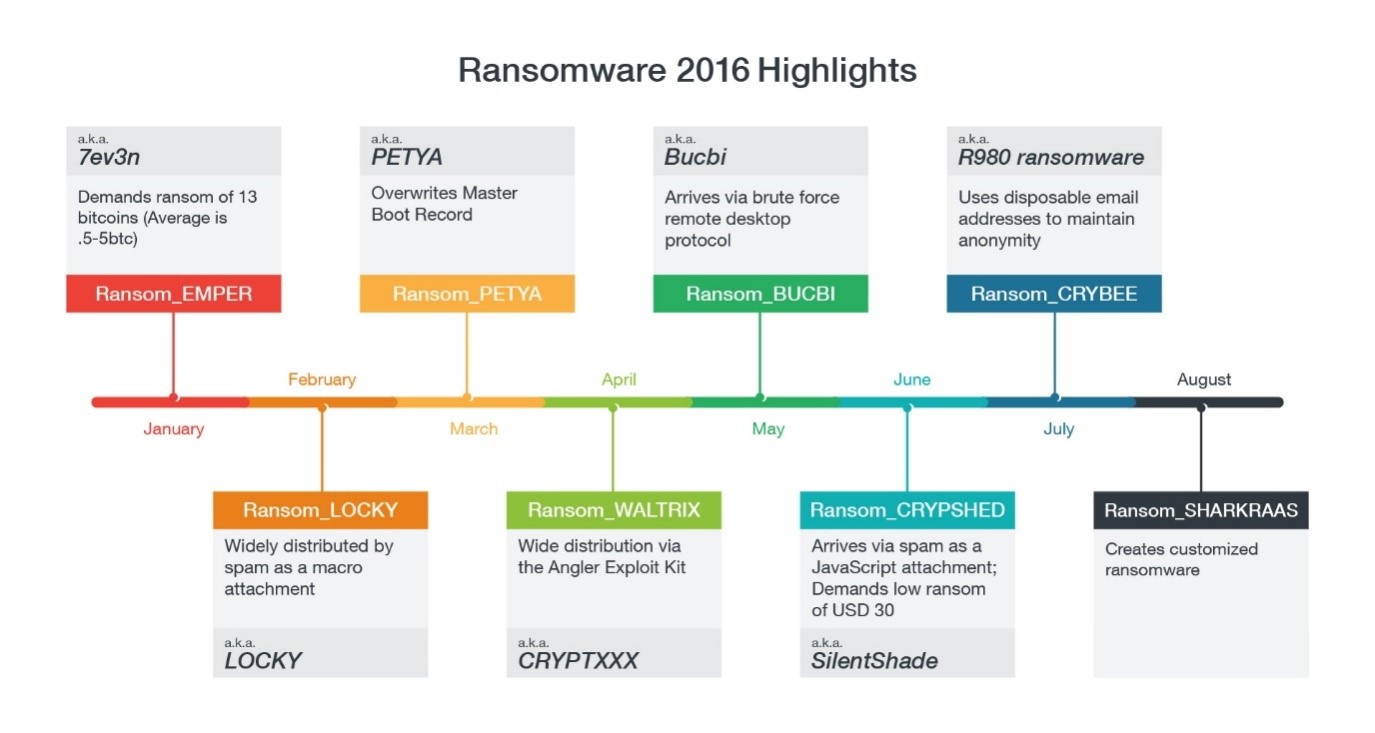
Source: http://www.trendmicro.com/vinfo/us/security/definition/Ransomware
There are several solutions adopted by organisations to prevent the ransomware infections. There are Email and web (Internet) gateway solutions. Email quarantine and web security are also steps to make organisations communication channels secure by blocking suspicious emails and suspicious web sites.
Ransomware Preventive Measures:
- Avoid opening unverified emails or clicking links embedded in them.
- Back up important files using the3-2-1 rule – create 3 backup copies on 2 different media with 1 backup in a separate location.
- Regularly update software, programs, and applications to protect against the latest vulnerabilities.
- Not only the computers, but other devices may also get infected by ransomware, e.g. Network-Attached Storage (NAS). If you are using a home use NAS and especially if it is connected to Internet, you are recommended to take the same preventive measures. You can refer to the official user manual of your NAS.



