Earlier this year, Trend Micro published a report about the security predictions for 2017 entitled “The Next Tier”. This report points out 10 predictions related to cyber security landscape.
It is predicted that Ransomware operations will break off as more variants are produced for deeper and wider attacks. Deeper attacks refers to planned attacks and wider refers to the impact on a range of devices as threat will affect non desktop targets like mobile and smart devices.
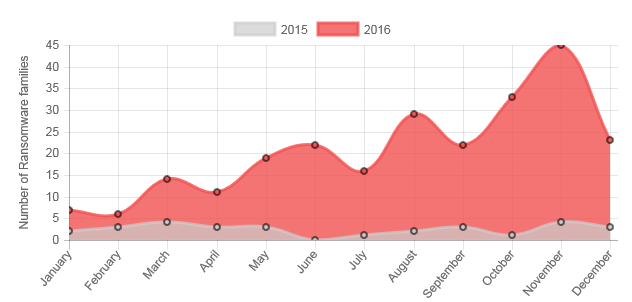
Ransomware Methods and Target Attacks Expected to Diversify
Trend Micro predicted in the past that 2016 would be a year of online extortion.
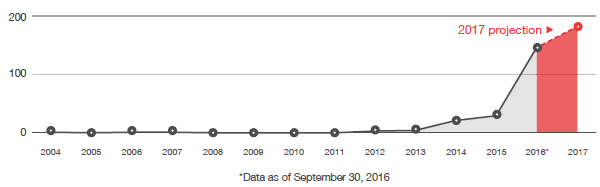
Above figure shows the annual number of ransomware families, including 2017 projection. It is expected that there will be an increase of 25% growth in the number of ransomware families in 2017. This trend is expected to translate to the increase in the number of cases related to ransomware.
There isn’t a 100% solution that can prevent or protect from ransomware. However, it is best to block the threat at its source, on the web or via email gateway solution. Machines learning technology can be applied to block the threat from its source by detecting suspected websites or a link to prevent the spread.
Machine learning is a type of artificial intelligence (AI) that provides computers with the ability to learn without being explicitly programmed. Machine learning focuses on the development of computer programs that can change when exposed to new data. The process of machine learning is similar to that of data mining. Both systems search through data to look for patterns. However, instead of extracting data for human comprehension (as is the case in data mining applications) – machine learning uses that data to detect patterns in data and adjust program actions accordingly.
Machine-learning technology is a useful solution against ransomware. A practical example of such solution is ICTO’s email quarantine service that detects unique and newly created ransomware and cyber threats.
It is predicted in the report;
- Business Email Compromise (BEC) will become cybercriminals favourite category to attack among others.
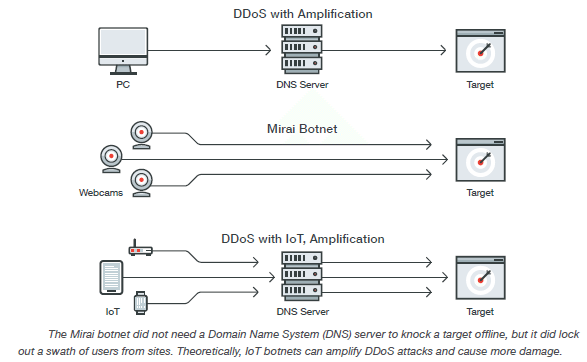
- Smart devices will play a role in massive Distributed Denial of Services (DDoS) attacks.
- Industrial Internet of Things (IIoT) devices will be targeted.
- Administrative costs will increase to implement the General Data Protection Regulations (GDPR) as cyber criminals will target networks to infiltrate with numerous motives.
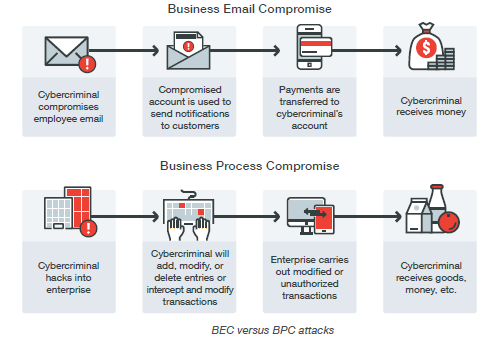
Business Email Compromise (BEC) Attacks
Business Email Compromise (BEC) refers hacking an email account or tricking an employee to transfer funds over to cybercriminal’s account. There is nothing special the only thing criminals require is an insight about an organization or individual to craft a believable email. Considering getting sufficient information requires only access to search engine, it only requires a query on a search engine.
It is hard to detect BEC attack. However, it is suggested that;
- Organizations should be able to block these threats using appropriate web and email gateway
- Implement stringent policies for normal and out of ordinary transactions to protect and prevent BEC attacks.
Business Process Compromise (BPC) to Target the Financial Sector
The figure shows about the BEC and BPC attacks.
Internet of Things (IoT) Devices and Targeted Attacks
IoT devices have brought efficiency in manufacturing and energy generation industries. Vendors are well aware of the environment. Point of failure should be identified and protected. In case there is an IoT attack, if intrusion prevention systems (IPSs) are in place, they should be able to identify and drop the malicious network packets.
Data Protection Regulations Raise Administrative Cost
Regulations regarding Data protection enforces organizations to inform users of their user rights and the changes if any due to new regulations. On other hand responsibility falls on organizations to make sure their users and their staff also follow those regulations. Data collection practices requires adjustments.
These changes enforces the organizations to review their data processing practices to fulfil the requirements and compliance accordingly.
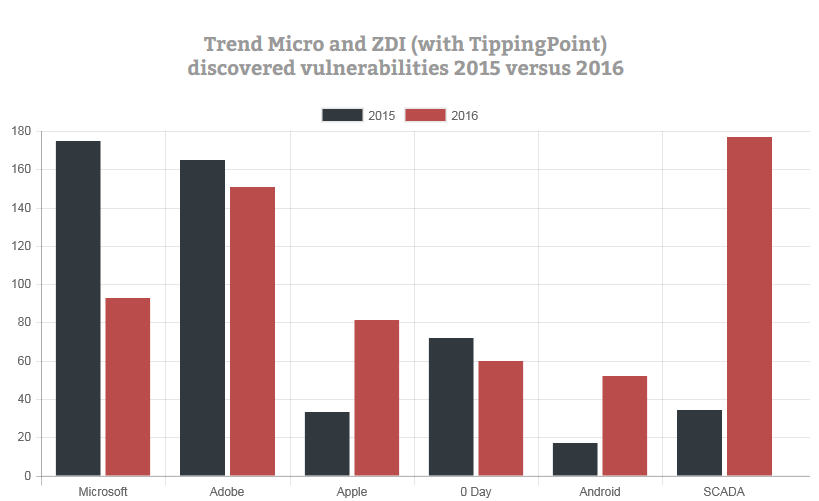
Platform Vulnerability
Vulnerability refers to flaws. Platform vulnerability encompasses the platform (Operating system or software). For example in 2016, Adobe has outpaced Microsoft in terms of vulnerability discoveries. Some system were perceived to be secure and free from vulnerabilities are not 100% secured as vulnerabilities appears to be rising. Cyber criminals have one objective and that is to make money faster. In the past, Microsoft was the major Operating System. Exploiting Microsoft’s flaws made the criminals reach a larger group. As Mac is gaining popularity, number of vulnerabilities are also on rise.
Lot of organizations continue to use unsupported or orphaned software. It increases the vulnerabilities.
Cyber Propaganda
Almost half of world’s population has access to Internet via smart phone, traditional computing device or via Internet Kiosks. Since more and more people have access to information without credibility check or source of it. Internet is also being used to influence public opinion. Social media is playing a greater role in peoples’ life. It has become a propaganda tool. It is predicted an increase in use, abuse and misuse of social media.
Threat Actors and Anti-Evasion Solutions
Improvements in technology placed organizations to place greater attention and effort on to IT security and administration. It is suggested not to stick to one security strategy instead consider to develop a cross generational multi-layered technology development.
Trend Micro’s report summarises as;
“IoT affords both risks and conveniences. Smart device users should learn to secure their routers before allowing any smart device to access the Internet through them. They should then include security as a consideration when buying a new smart device. These new challenges require a new take on endpoint security, a cross-generational security approach combining proven threat detection techniques for known and unknown threats with advanced protection techniques such as application control, exploit prevention and behavioral analysis, sandbox detection, and high-fidelity machine learning. Training employees against social engineering attacks and about the latest threats like BEC will complete the security culture needed to fortify an enterprise’s defenses for 2017 and beyond.”